

Johannes Franken
<jfranken@jfranken.de>
OpenSSH is an implementation of the ssh protocol suite. It's open source and continuously being developed further by the OpenSSH project team, see http://www.openssh.org
OpenSSH has been compiled for any operating systems, and is shipped with most linux or BSD distributions.
An excellent windows port using the CygWin32 libaries is available at http://www.networksimplicity.com/openssh/
| Name | Purpose |
|---|---|
| ssh | is the ssh-client. It initiates the connection to a ssh-server. See detailed description in the next chapters. |
| sshd | is the ssh-server. It accepts connections from ssh-clients. For details, see configuration notes |
| ssh-keygen | creates and converts keys. For details, see below. |
| ssh-agent, ssh-add |
keeps the decyphered privatekey in memory, where clients can access it. For details, see below. |
| ssh-keyscan | displays the hostkey of a ssh-server. For example uses, see below. |
Putty is free ssh client implementation, which - in contrast to the client that comes with OpenSSH - has got a graphical user interface. Get a version for Windows at http://www.chiark.greenend.org.uk/~sgtatham/putty/ . Finally, putty is available for Linux, too.
Of course, there are some commercial suppliers as well, e.g. http://www.ssh.com und http://www.f-secure.com On top of the possibilities of OpenSSH they contain programs for central configuration of servers, keys and tunnels.
jfranken@hamster:~ $ echo SSH-1.99-jfranken| nc -w 1 gate 22 SSH-1.99-OpenSSH_3.4p1Debian1:3.4p1-1\n[...] diffie-hellman-group-exchange-sha1,diffie-hell man-group1-sha1\0\0\0017ssh-rsa,ssh-dss\0\0\0faes128-cbc ,3des-cbc,blowfish-cbc,cast128-cbc,arcfour,aes192-cbc,aes256-cbc ,rijndael-cbc@lysator.liu.se\0\0\0faes128-cbc,3des-cbc,blowfish-cbc ,cast128-cbc,arcfour,aes192-cbc,aes256-cbc,rijndael-cbc@lysator. liu.se\0\0\0Uhmac-md5,hmac-sha1,hmac-ripemd160,hmac-ripemd160@opens sh.com,hmac-sha1-96,hmac-md5-96\0\0\0Uhmac-md5,hmac-sha1,hmac-ripem d160,hmac-ripemd160@openssh.com,hmac-sha1-96,hmac-md5-96\0\0\0\tnone ,zlib\0\0\0\tnone,zlib\0\0\0\0\0\0\0\0\0\0\0\0\0\0\0\0\0\0\0\0\0\0 |
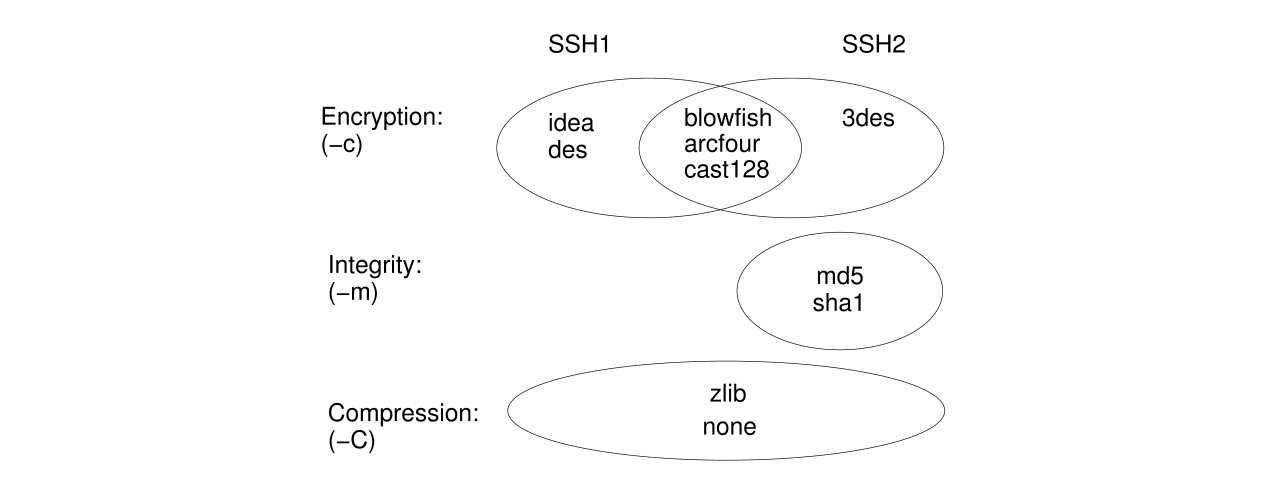
Here are some details for selected algorithms:
Host stunnel.our-isp.org ProxyCommand ~/.ssh/ssh-https-tunnel %h %p Port 443 Host hera 141.* User franken Protocol 1 Host 192.* gate mausi hamster tp Compression no Cipher blowfish Protocol 2 Host * ForwardAgent yes ForwardX11 yes Compression yes Protocol 2,1 Cipher 3des EscapeChar ~ |
| More about: see ssh(1), ssh_config(5) manpages. |
The ssh-server reads its configuration from:
| More about: see sshd(8), sshd_config(5) manpages. |
ssh hostname |
The authentication is done for your local username.
If you want to login as a different user, there's a couple of ways to do that:
| . | abandon the session, breaking down any tunnels. |
| & | abandon the session, tunnels stay open. |
| C | Shows you a prompt (ssh>), on which you can subsequently setup tunnels with the -L and -R commands (Details: see Teil 2). |
| <Ctrl-Z> | Suspend ssh. You are back in the shell from which you called ssh. Get back online with fg. |
| # | shows a list of connections that are tunneling on your session. |
| ? | Help. Also shows the other options, which I left out here, because I didn't find them too useful. |
If you're on a keyboard with deadkeys, you may need to press the tilde key twice for a tilde to pop up.
In case you are telescoping ssh sessions (one into another), you will get the n'th shell's escape mode (counting
from the outside) by pressing <Enter> and then the tilde key n (deadkeys: 2n) times. People finding
that too complicated can define different escape characters for each ssh, for example
<Ctrl-B>:
jfranken@gate:~ $ ssh -e ^B hamster jfranken@hamster:~ $ <Strg-B>. Connection to hamster closed. jfranken@gate:~ $ |
$ ssh tp -t vim /etc/hosts |
Here's some methods to use the blowfish-cipher in your local net, which relieves participating CPUs and thus speeds up communcations:
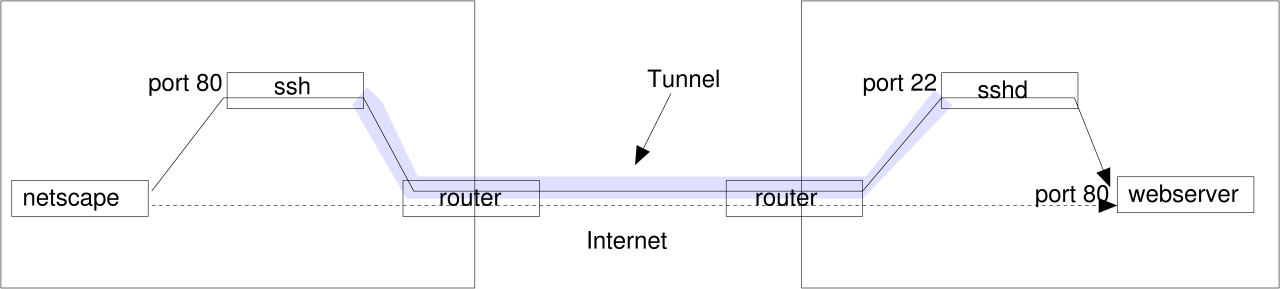
In contact to port-forwarding you can encrypt communications over unsecure network sections, being absolutely transparent for the client, which allows you to connect branches offices over the Internet:
To activate compression:
In contact to port-forwarding you can speed up communications over slow network sections, being absolutely transparent for the client:

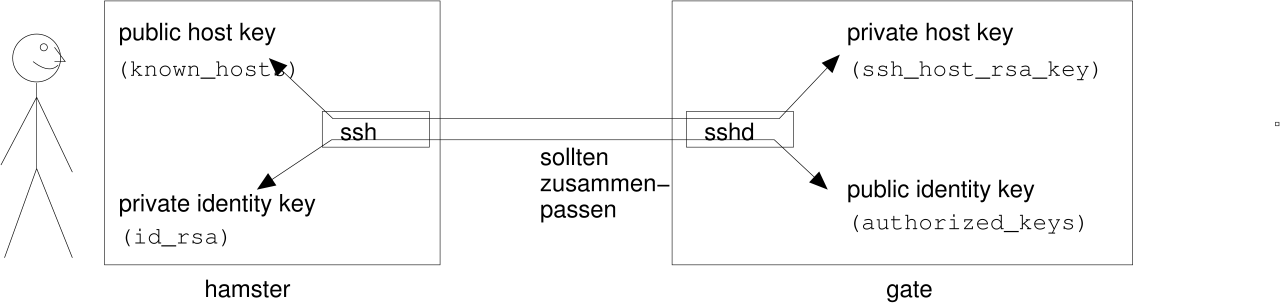
There are three different algorithms for this purpose:
| algorithm | parameter to ssh-keygen | Filenames | publickey starting with |
|---|---|---|---|
| RSA for SSH version 2 and up |
-t rsa | ~/.ssh/id_rsa[.pub] | ssh-rsa |
| RSA for SSH version 1 |
-t rsa1 | ~/.ssh/identity[.pub] | 1024 35 o.ä, (bits exponent) |
| DSA | -t dsa | ~/.ssh/id_dsa[.pub] | ssh-dss |
I'm not going into the specialities of each algorithm. Exctract is, that DSA generates most CPU load while RSA1 is easiest to crack. Thus, in common cases RSA would be a reasonable tradeoff.
Every public key (e.g. ~/.ssh/id_rsa.pub) consists of the following parts:
It will be uuencoded to fit 6 bit ascii, which makes it look like a single, long line of text. This allows you to
paste it into the text of an email.
ssh-rsa AAAAB3NzaC1yc2EAAAABIwAAAIEAxtWFO8XbyT6+IlBAWYyOb /VWraJ7iymKVsb0TNmieBSzF6fgustkT0nX3udbSqTqiEC/wXFKqeyl27 bkd+rEcFba+s+wgv9MKRaiV0kOFVQrAvwrKnS1QI6YZWZIhSP7KS5QE0H Rra+gy/47vGwHUn0RxksGOQ6YsKP5lNN8H3E= jfranken@hamster |
$ ssh-keygen -t rsa Generating public/private rsa key pair. Enter file in which to save the key (/export/home/jfranken/.ssh/id_rsa): Enter passphrase (empty for no passphrase): Enter same passphrase again: Your identification has been saved in /export/home/jfranken/.ssh/id_rsa. Your public key has been saved in /export/home/jfranken/.ssh/id_rsa.pub. The key fingerprint is: 7c:02:29:1c:d4:8a:90:ad:f2:b0:65:9e:71:92:ef:0f jfranken@hamster |
The fingerprint is a shared attribute of private- and publickey, and thus allows you to check which keys belong
together.
$ ssh-keygen -l -f .ssh/id_rsa 1024 5a:b6:c4:50:ce:ec:18:78:e9:b2:e7:5b:04:c2:e4:c7 .ssh/id_rsa.pub |
You can later change a private key's passphrase:
$ ssh-keygen -p -f ~/.ssh/id_rsa Enter old passphrase: Key has comment '/export/home/jfranken/.ssh/id_rsa' Enter new passphrase (empty for no passphrase): Enter same passphrase again: Your identification has been saved with the new passphrase. |
$ ssh-keygen -y -f ~/.ssh/id_rsa ssh-rsa AAAAB3NzaC1yc2EAAAABIwAAAIEA5+UaqG/zI... |
The client will then stop connecting, if the server's secret hostkey does not match the public key, which you had
stored on the client at ~/.ssh/known_hosts or /etc/ssh/ssh_known_hosts before:
jfranken@hamster $ ssh -o StrictHostkeyChecking=yes gate @@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@ @ WARNING: REMOTE HOST IDENTIFICATION HAS CHANGED! @ @@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@ IT IS POSSIBLE THAT SOMEONE IS DOING SOMETHING NASTY! Someone could be eavesdropping on you right now (man-in-the-middle attack)! It is also possible that the RSA host key has just been changed. The fingerprint for the RSA key sent by the remote host is 5c:6e:b2:99:3d:44:03:32:fb:e8:c1:ca:4f:cb:9e:8f. Please contact your system administrator. Add correct host key in /export/home/jfranken/.ssh/known_hosts to get rid of this message. Offending key in /export/home/jfranken/.ssh/known_hosts:45 RSA host key for gate has changed and you have requested strict checking. Host key verification failed. jfranken@hamster $ |
jfranken@hamster $ ssh -o StrictHostkeyChecking=yes gate No RSA host key is known for gate and you have requested strict checking. Host key verification failed. jfranken@hamster $ |
If you don't want to add all those hostkeys to your known_hosts-file by hand, but just be warned about
changes, you can set StrictHostkeyChecking to ask:
jfranken@hamster $ ssh -o StrictHostkeyChecking=ask gate The authenticity of host 'gate (192.168.42.1)' can't be established. RSA key fingerprint is 5c:6e:b2:99:3d:44:03:32:fb:e8:c1:ca:4f:cb:9e:8f. Are you sure you want to continue connecting (yes/no)? yes Warning: Permanently added 'gate,192.168.42.1' (RSA) to the list of known hosts. jfranken@gate $ |
The lines of known_hosts are of the following format:
sshd will look for the hostkeys at these places on the server:
You can generate these keys with the ssh-keygen tool. Just be sure to provide an empty passphrase to the privatekey. At most distributions this job is typically done by the install script of the sshd package.
When the hostkey of a server changes (for example after upgrading to a newer version of OpenSSH), you may need to
remove the corresponding lines from your known_hosts files on the client.
| More about: see: sshd(8) manpage |
If you have got to enter quite a number of hostkeys to some known_hosts file, have ssh-keyscan do the job for you.
Because failures to read the hostkey point to network- or server-problems, you can run ssh-keyscan to
detect such issues: if it does not display the hostkey, there is a problem.
| More about: see: ssh-keyscan(1) manpage |
Advantages of public key- over password-authentication:
Using public keys for authentication is easy: XXX TODO
At the beginning of each line in ~/.ssh/authorized_keys you can tell sshd from wich hosts a public key can be used and what special options (environment settings, shell, etc) to use. The exact syntax is as follows:
If the server option PasswordAuthentication No is set in /etc/ssh/sshd_config, the use of
public keys becomes mandatory, which gives you pretty good security against brute-force attacks.
| More about: see: sshd(8) manpage |
jfranken@hamster $ ./ssh-copy-id2 franken@hera.cs.uni-frankfurt.de franken@hera.cs.uni-frankfurt.de's password: Now try logging into the machine, with "ssh 'franken@hera.cs.uni-frankfurt.de'", and check in: .ssh/authorized_keys to make sure we haven't added extra keys that you weren't expecting. jfranken@hamster $ |
| More about: see: ssh-copy-id(1) manpage |
If you call ssh-agent without parameters, it will create an unix-domain-socket, tell you, how to reach
it, and listen on it in the background.
$ ssh-agent > myagent.sh $ cat myagent.sh SSH_AUTH_SOCK=/tmp/ssh-XXcMloql/agent.21753; export SSH_AUTH_SOCK; SSH_AGENT_PID=21754; export SSH_AGENT_PID; echo Agent pid 21754; |
Use ssh-add every time you want to teach ssh-agent one of your private keys:
$ . ./myagent.sh Agent pid 21754; $ ssh-add ~/.ssh/id_rsa Enter passphrase for /export/home/jfranken/.ssh/id_rsa: Identity added: /export/home/jfranken/.ssh/id_rsa (/export/home/jfranken/.ssh/id_rsa) $ |
Use ssh-add -l to get a list of any keys that that ssh-agent knows, or ssh-add -L to retrieve all corresponding public keys.
When connecting, the ssh-client will then try the private keys from ssh-agent first, instead
of those from the identity files:
jfranken@hamster $ . ./myagent.sh Agent pid 21754; jfranken@hamster $ ssh gate [...] debug1: userauth_pubkey_agent: testing agent key /export/home/jfranken/.ssh/id_rsa debug1: input_userauth_pk_ok: pkalg ssh-rsa blen 149 lastkey 0x80926f8 hint -1 [...] jfranken@gate $ |
$ /usr/sbin/lsof -a -u jfranken -U -c ssh-agent COMMAND PID USER FD TYPE DEVICE SIZE NODE NAME ssh-agent 477 jfranken 3u unix 0xc1da1aa0 1155 /tmp/ssh-XXWzoqlO/agent.452 $ export SSH_AUTH_SOCK=/tmp/ssh-XXWzoqlO/agent.452 SSH_AGENT_PID=477 |
| More about: see: ssh-agent(1) manpage ssh-add(1) manpage |